Blesta 3.0: The Translator (Update)
In January we announced the availability of a language crowdsourcing project, the Blesta Translator. The goal of the project is to facilitate the translation of Blesta into many languages, and to ship these languages with Blesta, starting with version 3.
This week we made a few additional changes live, and they are –
- Added Nederlands, NL (nl_nl) to the list of available languages
- Added a machine translation (Google) for reference
- Added “In Order” and “For Confirmation” translation methods
- Added some context to language strings including terms, filename, and type

#2 Machine Translation
The machine translation is available for all translation methods, “Random”, “In Order”, and “For Confirmation”. By default it is not displayed, but will be shown when a link is clicked. The idea is that it may be useful to see the Google translation, but that it shouldn’t be relied on, or copied without forethought.
#3 Additional Translation Methods
The goal of the translator isn’t simply to get translations, but to get good translations.
When different people translate a term identically, it has a higher weight than terms that are only translated by one person. Such terms become “confirmed”, and are trusted to be more accurate. So, the “For Confirmation” translation method displays the best possible translations by other people. One of these translations can be accepted by clicking on it. Alternatively a different translation may be entered like normal.
The “In Order” translation method is pretty self-explanatory, terms are given in alphabetical order with the goal of completing a translation. This means that some terms may be skipped initially until the translation is completed as a whole. Once the translation is completed, terms that were intentionally skipped will be presented.
The end goal is to make several translations available. A version translated wholly by a specific person, a confirmed only translation that may be missing some terms (missing terms are shown in the default language), or a complete translation consisting of confirmed only or both confirmed and unconfirmed terms. The latter are the ones we will include with Blesta by default, but all will be available for direct download in the future.
Thanks for reading! If you know another language, please sign-up and contribute
Video next week? Probably.
Related Tags:
Blesta 3.0: Automation
Part of my job in the development of v3 is to take a step back and consider how each and every feature in Blesta can be improved over previous versions. Lots of thought, and many discussions surround even the simplest details of both the external and internal workings of Blesta, the visible and invisible.
Today I want to compare and contrast, and reveal how we handle automation in v3.
v2
Version 2 has a Cron Status & Setup page, under Settings > API/Cron Settings. The intent of this page is to show you when the cron last ran, how to set up your cron, and provide a method by which to run the cron manually. We were the first to secure the cron with a key, preventing it from being run by unauthorized users. Overall very basic, and it works pretty well.
v3
Version 3 does everything mentioned above, but in a simpler, more intuitive way — with the addition of being able to update the cron key right here. This key is now separate from the API key, which it shared in v2.

This is a good replacement for v2, and we could have stopped there.. but like I said in the opening, a lot of thought, many discussions.. and I’ll add, a lot of planning and development time goes into each and every feature.
One thing that bothers me a lot with v2 is that I can’t set exactly when I want a particular task to execute. Some tasks run once daily, some run every x minutes. The daily tasks run every day at midnight, and for the most part, the more frequent ones are at the mercy of how often the cron is scheduled to run.
This creates some issues, first of all is that midnight emails probably don’t have the highest read rate. Secondly, midnight account suspensions for non-payment result in emergency tickets at a time when most of your staff is sleeping or in the shower.
So, the actual cron job should run every 5 minutes, and you should be able to schedule when each task runs. Right? We think so. It’s almost common sense, but nobody has done it until now.

…
Above is what Invoice Creation and Auto Debit tasks look like. In this case, we have them both set up to run at 2pm daily. These are 2 tasks out of more than a dozen.
What about more frequent tasks?

This option illustrates how paid pending services, such as exist when a new order is placed, are provisioned.. every 5 minutes.
In addition to being able to schedule each task, they can also be explicitly disabled.
Developer Candy: Plugins can register automation tasks.
Another important thing to note is that all the times are in your local timezone — or whatever you set your timezone to be, regardless of the server time. Additionally, all dates and times in Blesta everywhere are stored in the database as and converted from UTC, which means you can change your timezone without affecting the stored value.
The default options will be perfect for most people, and there will be no real necessity to dig in and tweak these around.. Really, it’s not that important, but I wanted to show you for two reasons. 1. It’s a neat, practical feature and more importantly.. 2. It gives you a glimpse into how we work, how detail oriented we are, and how serious we are when it comes to usability.
Hope you have a nice weekend. Speaking of weekends…
Nerd Alert: If you play a game called Minecraft, we’ve got a Minecraft server up and running at 74.80.216.146. Come join us, some of our friends, and some of their friends as we build random stuff. HostMaster = Me, Awesomisitist = Tyson, Codelphious = Cody.
Related Tags:
Blesta 3.0: Invoice Customization (video)
Cody posted an article last week on Software Licensing, which I found amazing. Be sure to check it out if you haven’t already.
This week I’ve got another video, and it’s all about options available for invoices. There are many improvements in v3 when it comes to invoices, so I thought you might like to see what we’ve got cookin.
- Two all newly designed invoice templates available.
- Invoice formats are now available. Add a prefix, suffix, and/or the year to invoice numbers.
- Set or change the next invoice number anytime.
- Have invoice numbers increment 1 at a time or in multiples, ie Invoice # 5, 7, 9.
- Pad invoices to a specific length, ie Invoice # 00001, or xxxx1.
- Add your logo, a background image, and company name and address to invoices.
- US Letter, and A4 paper sizes now supported.
- A PAID watermark can now be displayed on paid invoices.
Invoices are flexible yet simple, fully internationalized, clean, and they print beautifully. I’m really happy with the changes we’ve made to invoices since 2.x and I hope you are too!
The video is below, as usual you can make the video full screen, and be sure to turn on your sound.
Related Tags:
Blesta 3.0: Software Licensing
Software licensing offers software developers a means of ensuring their product is not installed without prior authorization (generally by purchasing the product). Some competing products offer licensing modules to facilitate the deployment of such software, but their designs are critically flawed in a number of ways. Today I’ll describe the software licensing scheme we use in Blesta 3.0, and why it works. But first, let’s take a look at the problem.
To ensure an installation is allowed to run it needs to established its authenticity. This is generally done by “calling home.” That is, by contacting the licensing server. Information returned from the licensing server varies, but generally contains data about how, when, and where the software can run.
The naive approach
It goes without saying that if the license data can be tampered with one can easily bypass the license check. To resolve this, others have devised a scheme whereby the data is hashed using a shared secret salt know by the licensing server and by the product. When the product receives the license data it creates a hash from the data using the shared secret salt and compares that hash with the one that accompanied the data. If the two hashes match the data is trusted, otherwise the data is rejected.
Some systems don’t even bother sending the original hash of the data and instead compute and store the hash upon arrival for future reference. These systems are even less secure.
There are a number of exploits with these systems:
- Because the same shared secret is used to generate the hash across all installations it may be possible to obtain the shared secret
- Because the hashing method generally used is insecure it may be possible to tamper with the data and still produce the same hash (i.e. a hash collision)
- Because the data passed across the line is unencrypted or poorly encrypted it may be intercepted and the licensing server may be tricked into returning data regarding a separate valid license, or the licensing server may itself be spoofed
Exploiting it
Some may argue the dangers of revealing how insecure systems can be compromised, just as a magician might jeer at the sight of someone exposing their trickery. Those that argue from that position fail to realize that security does not arise out of obfuscation. Shannon’s maxim teaches that one must always assume that an attacker understands exactly how a system operates.
- Determine where the software calls home to. This can be done by monitoring network traffic or guessing the license server domain.
- Spoof the licensing server by modifying the server’s DNS or hosts file to resolve to a “license server” you create.
- Capture the data sent to the licensing server to a log file.
- Capture the data returned from the licensing server. This can be done by manually passing the data from #3 to the licensing server. Note that if you do not have information to obtain a valid response from the license server, you may be able to obtain that information from another user with a valid license or from a public demo of the application.
- Return the license data you capture from the license server, or modify it to ensure it continues to function ad infinitum.
The solution
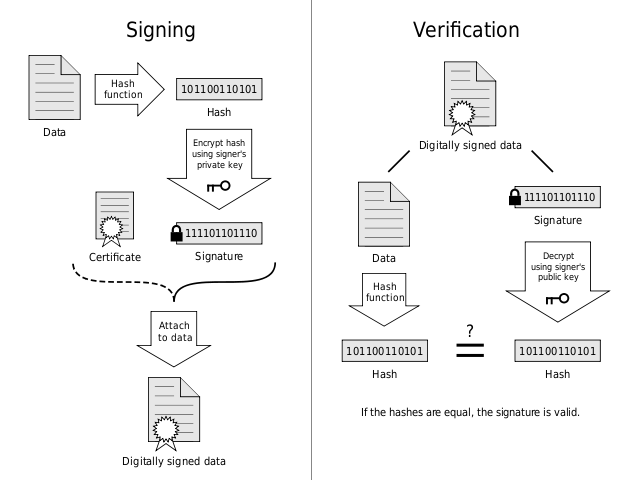
A digital signature allows us to verify the authenticity of a message through the use of an asymmetric key cipher, which uses one key (the private key) to encrypt data and an entirely different key (the public key) to decrypt data. Meaning that an attacker can not reproduce signature data since they do not have the private key.
How it works
- The license server generates a unique public/private key pair for the installation and delivers the public key securely to the installation
- The license server then encrypts the license data, generates a hash of the data and encrypts it using the private key to produce the signature
- The license server then delivers the data and signature to the installation
- The installation verifies the signature by decrypting the signature with the public key and comparing it with the hash it generates from the data
In the event that the signature can not be verified the license data is rejected and the license becomes invalid. Attempting to spoof the license server does nothing because only the license server can sign messages and the installation will only be able to verify signatures from the license server.
Additionally, at any time the license server may choose to generate a new key pair. This is especially useful because as attacks on asymmetric key ciphers becomes computationally cheaper it becomes increasingly important to cycle keys and/or increase key lengths.
Why are we telling you all this?
It would be great if there were no need for software license validation, but there is and there’s a market for it. Our philosophy is if you’re going to do something you ought to do it right. At the moment, thousands of developers put their software in the hands of licensing systems that provide illusory protection at best, and that’s unfortunate.
So, why are we telling you all this? Because we’re building a licensing plugin for v3 that does it right. We don’t mind sharing with everyone how it works because even licensing systems should be transparent. And, if our competitors decide to rework their licensing systems and do things right — then everyone is better off. And that’s what it’s all about.
Blesta 3.0: Staff Calendar (video)
It’s been a while since I posted a video, I missed you. So, today — a new video, about the Staff Calendar. Staff Calendars feature the following:
- Mini dashboard calendar with badges that indicate the number of events for each day.
- Full size monthly, weekly, and daily calendar.
- Shared events, staff members can share events with everyone on their team, or keep them private.
- Multi-day, whole day, and time based events are supported.
- Intuitive drag-n-drop interface to create and edit events.
We hope you like the calendar, I know our team will be using it! Developer tidbit: Yes, you’ll be able to add events to the calendar from your custom plugin. I know people are going to ask so I’ll tell you.. recurring events are planned for a future release.
The video is below, as usual you can make the video full screen, and be sure to turn on your sound.
